Understanding the WannaCry bitcoin ransomware attack
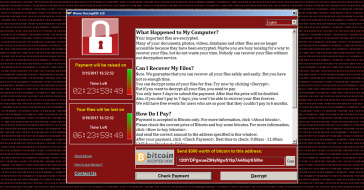
If you’ve recently been following digital currency news, then chances are that you’ve heard that one of the world’s biggest digital currency-based ransom attacks is currently underway. The ransomware attack, known by the name of WannaCry, has reportedly managed to infect over 220,000 computers in 99 countries so far, thus being referred to as unprecedented in its scale by the Interpol.
For those who do not know, WannaCry is based on the EternalBlue exploit, developed and leaked by the U.S. National Security Agency, capable of gaining access to the hard drives of any Windows computers, and locking users out of their PCs, by encrypting all their data. Upon being infected by the ransomware which has managed to spread through email attachments, and local area networks, infected computers will display a message written in 28 languages, asking the user to pay a sum in Bitcoin, to regain access to the computer and its afferent data.
This ransomware attack has made Microsoft release patches for all its operating systems, including Windows XP, which they stopped supporting a while ago. Regardless of the magnitude of this attack, it seems like the bitcoin extortionists haven’t managed to gain access to a lot of money. According to Chainalysis, a company that works with law enforcement agencies, bitcoin companies and banks to analyse the blockchain for various forms of financial crimes, has stated that the hackers are receiving funds to three main addresses, which have been actively tracked by the community, to help determine how much money they’ve managed to extort so far.
It seems like at the time of writing, the three bitcoin addresses have managed to receive a total of around $23,000, which definitely isn’t high considering the 220,000 infected computers, and the price of $300 associated with the decryption keys. Currently, it seems like people in Russia and South Korea are the ones who’ve sent the most money out to the extortionists, to regain access to their computers.
Based on everything that has been outlined so far, as the attack is still in progress, it is important to patch up your operating system, and antivirus, while also avoiding to open suspicious emails and their attachments. What do you personally think about the magnitude of this attack? Let us know your thoughts in the comment section below.
Source: Read Full Article
